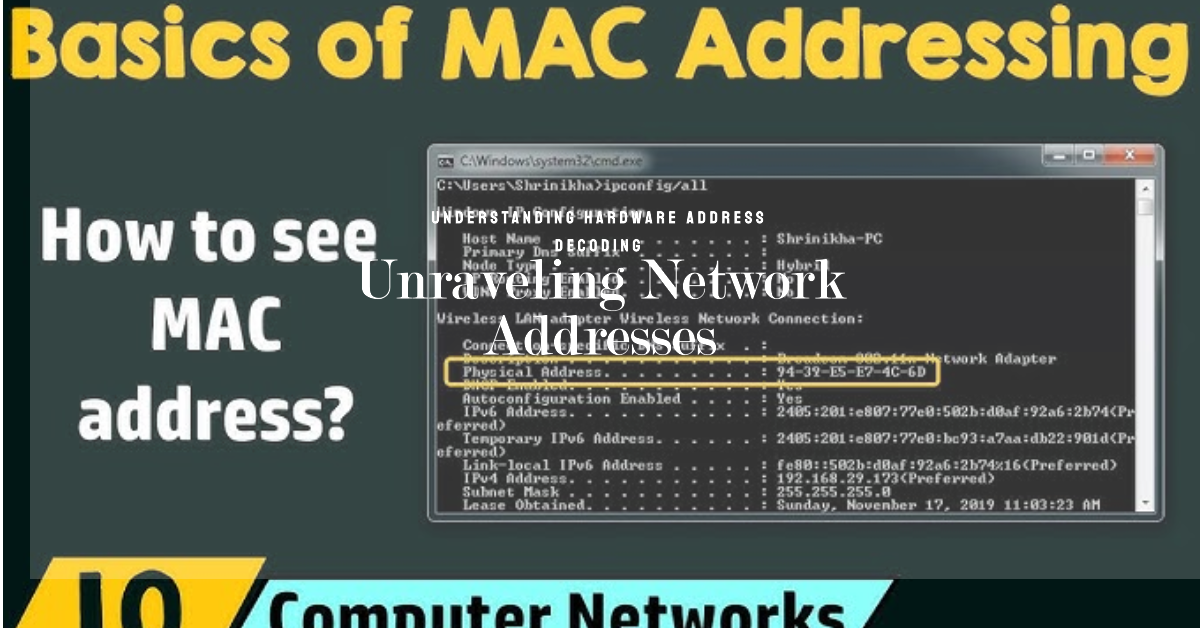
Unicast MAC addresses are unique 48-bit hardware addresses. The team assigns them to network interfaces to find devices on a local network. They enable direct communication between devices. They safeguard data frames on their journey to their destinations. This vital process guarantees accurate delivery, maintaining information integrity and security throughout transmission. Every network-connected device has a unique unicast MAC address. It is a vital identifier in digital communication systems. It allows precise communication between devices.
What is a Media Access Control address?
From the assembly line to global networks, each device has a digital fingerprint. Its interface is the fingerprint. This indelible mark, etched by manufacturers, is the MAC address. Hard-wired into hardware, it’s a permanent signature. It’s the key to recognition as devices traverse diverse digital landscapes. It ensures unique identification across the interconnected world. It remains unchanged unless someone modifies it by hand. Such changes are rare. On local networks, Wi-Fi devices sport unique tags called MAC addresses. Hexadecimal codes, spanning 12 characters, serve as unique network identifiers. These MAC addresses, such as 00:1A:2B:3C:4D:5E, distinguish individual devices. Unicast MACs ensure each network-connected gadget has its own digital fingerprint. They use a base-16 system, with six pairs of digits and letters, 0-9 and A-F. This gives each device a unique address.
Structure of a MAC address
A common MAC address features two divisions:
Not possible to remove the adverb.
Suppliers determine the opening 24 bits of MAC addresses. They identify devices in a way that is unlike any other. For example, a manufacturer like Apple or Dell will have its own unique OUI. This helps to identify the brand or company that made the device.
Device-specific identifier
The last 24 bits, or the last three sets of characters, serve as a unique identifier for the device. The manufacturer assigns this to ensure that each device has unique address.
The MAC address 00:1A:2B:3C:4D:5E, split in half, reveals a hidden narrative. This unique identifier, a digital fingerprint, whispers secrets of its origins and purpose. Each segment, crafted with precision, holds a piece of the puzzle. Unraveling its meaning, we glimpse the intricate world of network communication. Its opening act, 00:1A:2B, betrays the manufacturer’s signature. The closing scene, 3C:4D:5E, stars the device in its maker’s cast. This digital fingerprint gives each product a unique ID in the vast network. Like actors on a stage, MAC addresses perform their roles. They ensure each device is distinct in the grand production of interconnected systems. Devices in networks rely on MAC addresses for data exchange. These unique identifiers enable precise packet routing. Network interfaces receive all packets but only process those matching their MAC. This system enables efficient, targeted communication across the network. It allows devices to send and receive data with precision.
Ethernet Communication:
Frames, tiny data packets, zip through Ethernet networks. Every frame carries a distinctive fingerprint: origin and endpoint MAC identifiers. These digital fingerprints guide your computer’s messages, ensuring they reach their intended target. Like precise postal codes, MAC addresses direct data traffic. They keep communication swift and accurate on the network’s busy highways.
Wi-Fi Connections:
Wireless networks rely on MAC addresses for device identification. Smartphones, laptops, and routers all have these unique identifiers. Upon connecting to Wi-Fi, a router recognises each device by its MAC address. It then communicates with it, enabling seamless network interaction. Some networks use MAC address filtering. It limits access to devices with specific MAC addresses.
When a device knows only an IP address, it employs ARP to uncover the corresponding MAC address. This Address Resolution Protocol joins IP and MAC. It enables vital device communication on networks. The device sends an ARP request, asking “Who has this IP address?” The IP-queried device replies without delay, revealing its unique MAC address. This allows the sender to address the data in the correct manner.
Why are MAC addresses important?
Unique Identification:
MAC addresses give each network device a unique ID. This uniqueness is crucial. It allows devices to send data to the right destination without confusion.
Network Security:
You can also use MAC addresses to manage security on a network. For example, MAC address filtering lets admins control Wi-Fi access. Network admins wield MAC filtering power. This tool controls access to specific devices. It enhances security and network connectivity. While this can help control access, it is not foolproof. Attackers can “spoof” or change MAC addresses.
Troubleshooting:
MAC addresses are helpful when diagnosing network problems. Network admins can fix issues faster by finding the devices that send and receive data. They can trace problems with greater speed.
Tracking Devices:
Network giants often harness MAC addresses to watch devices. This practice aids asset management and bolsters security by flagging unauthorised gadgets. Tracking is very effective in large corporate networks, where device control is key. Can someone change MAC addresses?
Most devices have a hard-coded MAC address. But it is possible to change or “spoof” it using software. This is sometimes done for privacy or to bypass network restrictions. Yet, it is not usual for many users. Changing a MAC address can cause network issues or security risks if it is not done with caution.
Limitations of MAC addresses
On local networks, MAC addresses are unique device IDs. They help connect devices and control linked equipment. This optimises communication channels, enhancing system performance and responsiveness. But they have some limitations:
Limited to Local Networks:
Devices use MAC addresses only within local networks. They do not work for routing data across the internet or between different networks. For this, they use IP addresses. We design them for global communication.
Security Risks:
MAC addresses are usually unencrypted. So, malicious actors can intercept or spoof them. They are less secure for identifying devices on a network than higher-layer IDs, like IPs.
No direct use for routing:
- MAC addresses are vital for local communication. But routers use IP addresses to forward data between networks. MAC addresses are for local network gossip only. They do not pass data across the internet.ConclusionMAC addresses are vital identifiers for network devices. They enable smooth communication across digital networks. These unique identifiers, particularly unicast MACs, guide data to its intended destination. In Ethernet or Wi-Fi setups, MACs ensure precise packet delivery. MAC addresses are vital in local network communication. MAC addresses enable smooth interactions between nearby devices. They are vital for efficient local data exchange. Devices use these unique identifiers to interact without interruption. Each hardware component carries its own digital fingerprint, enabling precise data routing. Networks function due to these built-in codes. Without MAC addresses, local connectivity would fail. Devices wouldn’t recognise each other. But they have limits in security and global routing. Knowing how they work can help anyone in networking. This solution boosts security, streamlines management, and aids troubleshooting. It also improves network performance in key areas.
FAQs
Can someone change a MAC address?
Yes, most users rarely change or “spoof” a MAC address using software. It’s done in some cases, like for privacy or network troubleshooting. But it can cause issues if not done with care.
What is the difference between unicast and broadcast MAC addresses?
A unicast MAC address sends data to one specific device on the network. A broadcast MAC address sends data to all devices on the network at once. Unicast implies a personal exchange, whereas broadcast conveys to a larger audience.
Do MAC addresses function in digital communication?
Within local networks, MAC addresses reign supreme. They orchestrate device communication, enabling seamless interactions. But their influence ends at the network’s edge. Beyond this boundary, other protocols take over, guiding data across vast digital landscapes. . For communication between networks or the internet, devices use IP addresses instead.